Configuring Provided REST APIs
As part of setting up a Provided REST API, it is necessary to change the encryption key and configure the authentication settings in the appsettings.json files. Before we can change the keys required in these files, we need to generate the keys with the Setup tool. Learn how to generate these keys on the Generating Keys page.
The generated key can be copied to replace the default key in the appsettings.json file. Please generate and use a unique key for each Provided REST API.
REST API appsettings.json
- Navigate to the following directory: ..\<AMT_Environment>\Apps\<APPLICATION>\Binaries\Common\RestApiProvider\<Name of the Rest API>\.
- Copy the appsettings_default.json file found in this directory and rename the copied file to appsettings.json (overwrite the previous exiting file if required).
- Open the appsettings.json file in a text editor and configure the settings listed below.
- In the Amt section:
- AmtCookieEncryptionKey
- BusinessLogic {
- ApplicationName (the name of the AMT application)
{ "Amt": { "AmtCookieEncryptionKey": "YGQ9zlT4noYK3O3+SnsbuNyalJMhGpXvZ3Zr82xgE8I=", ... "Businesslogic": { "ApplicationName": "CUSTOMER_MANAGEMENT" }, ...
- In the Authentication section:
- AuthenticationType - Set to "JWT" (JSON Web Token)
- Authority - Enter the URL of the authorization server.
- Audience - Set the configured intended recipient of the access token.
- NameClaimType - The claim type that will be used to identify the user. Commonly preferred_username is used as claim type.
"Amt": { ... "Authentication": { "AuthenticationType": "JWT", "JWT": { "Authority": "https://login.example.org/amt-applications/v2/auth", "Audience": "amt-provided-restapi-demo", "TokenValidationParameters": { "NameClaimType": "preferred_username" } }
- In the Amt section:
- Save the file.
Recycling Application Pools
In order to apply the new settings, a restart of the application pools is needed for all Provided REST APIs to function properly.
It is possible to only restart the individual application pools of the applications where the appsettings.json file was modified.
Which, in this case, is the application pool of the newly created Provided REST API.
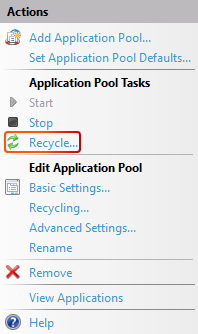
Click on the application pool that needs to be recycled and select Recycle....
Alternatively, it is also possible to restart the whole IIS which also recycles every Application Pool.
The downside is that this will affect every Web Application hosted on the IIS instance.