Encryption
This option offers the possibility to enable AMT encryption and manage
encryption keys. When the Use encryption checkbox is NOT checked, old style Lion 5.3 encryption will be used for
encrypted fields in all application in this environment. When checked secure AES encryption will be used, once
configured correctly.
AMT encryption comes with a COM Module for the encryption of data and
encrypted transmission from the application server to AMT Screens or the Webclient.
To enable the use secure AES encryption throughout the environment, click the 'Edit' button in the upper
left, check the use encryption checkbox and click the 'Apply' button.
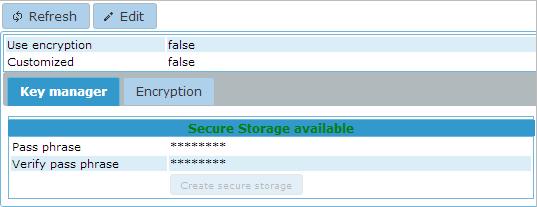
Before keys can be created an encryption database has to be present. To do this create an empty database, register the
database in the Databases page of the
ControlCenter with the type set to encryption and perform a reorganization on this database.
After creation of the database secure access to this database has to be enabled by creating a encryption key for the
Key manager. Click the 'Edit' button, enter a Pass phrase in the Key manager tab of sufficient length (minimal 20
characters), click the 'Create secure storage' button and click the 'Apply' button.
To enable encryption of the data itself now at least one encryption key has to be stored in the encryption database.
To do this click the 'Edit' button in the upper left, go to the Encryption tab and enter a Pass phrase as shown
below.
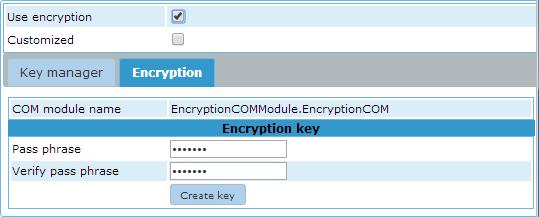
Then click the 'Create key' button and the 'Apply' button. An encryption key has now been created and will be
used on all new encrypted fields.
It is possible to add more then one key, automatically the latest key will be used for new encryptions. A reference to
the used key will be stored with the encrypted data so the right key will be used for decrypting data. For
that reason there is no functionality to remove or change keys. When keys are manually removed or
changed all data encrypted with that specific key is lost forever.
If wanted custom encryption can be used by providing the functionality of the COM Modules in two custom COM Modules.
How this can be configured is described in Creating Custom encryption COM Module. In any other case the checkbox
Customized should be left unchecked to ensure the use of the provided COM Modules.
For more detailed information on implementing encryption see Data Encryption.
